Over the last 2 weeks, starting on 10/19/2022, Zettasecure has seen a sharp increase in bruteforce attacks against Synology NAS systems of its own customers, as well as various hosted honeypots. These attacks initially focused on specific usernames such as “admin”, “syno”, “synology”, or “administrator” and then changed last week into a more general direction to standard names such as “eden”, “peter”, “joyce”, etc.. There is obviously an attempt to get a successful login. We tested what the attackers did with it and could see that after a successful compromise, all data is stripped off and then appears in an encrypted split folder. All other files were completely removed. Bitcoins are then demanded for the password. This is a variation of a ransomware attack.
The data obtained was used to create a heat map of the countries from which the attacks originate in order to plan more targeted measures against them, if necessary.
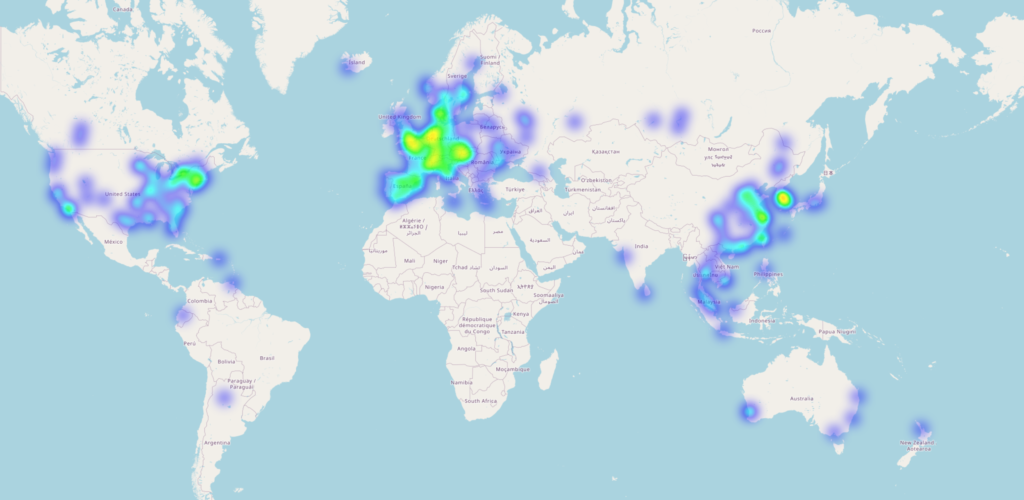
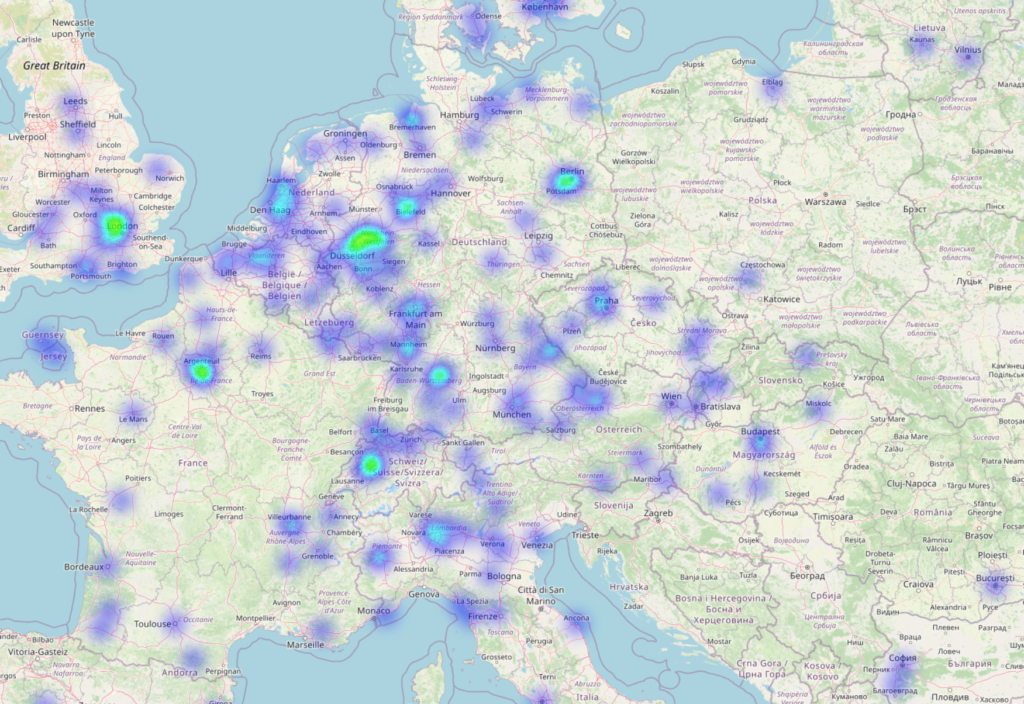
It is immediately apparent that the focus is coming from European countries and that GeoIP blocking would only reduce the impact, but unfortunately cannot prevent it. If you take a closer look at Austria and Germany, both countries are equally affected. This approach is therefore not a solution for this attack.
How to protect yourself from this attack now?
The easiest way would be not to expose a Synology NAS directly to the Internet. This way, attackers would not find it and could not launch an attack. However, it is sometimes necessary to publish a NAS on the Internet directly. The following methods can be used for this purpose to minimize the risk of attacks:
- Do not use default users and first or last names. Deactivate the default admin account “Admin” and set your own.
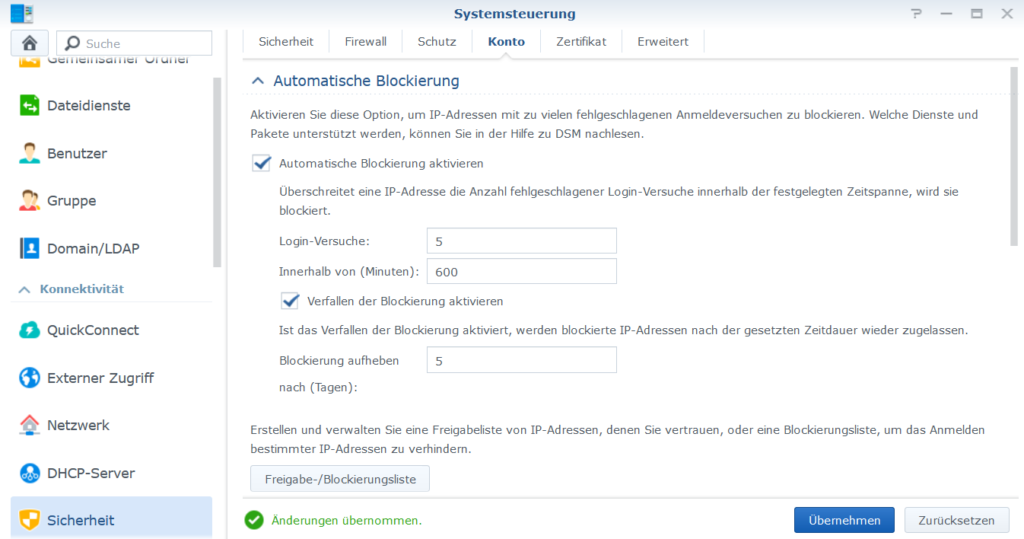
- Increase the time for automatic blocking of IP addresses under “Control Panel” -> “Security” -> “Account” -> “Activate automatic blocking”. Use 600 minutes and 5 login attempts for this. We found that each IP address is used 32 times in 24 hours, but the default values do not work, because they only work for fast attacks.
- Enable 2-factor authentication under “System Controls” -> “Users” -> “Advanced”.
- You are free to use GeoIP blocking to reduce the impact and filter to your own country. However, it is not a solution for this type of attack.
- Alternatively, you can additionally use an IP blocklist. Unfortunately, this does not protect against new attacks, which is why we advise against it at this point.
- Use a VPN and only allow connections from your own gateway. We can help you with that.
- Update your current DSM version to prevent known attack paths.
- Occasionally it has helped to change the default ports 5000 and 5001.
- Check if you are also affected by this attack by using our IoCs. For this attack, you can find them at https://github.com/Zettasecure-GMBH/IoCs/tree/main/Synology%20Bruteforce%20Attack
You would like to receive these and even more analyses faster and more timely? We would be happy to support you in blocking and preventing these and other attacks in their entirety. Just contact [email protected] and ask us your questions about this and other topics.





